Describe the Three Factors That Can Be Used in Authentication
As threats become more sophisticated it is critical to have strong authentication in place from the policy process and. Determines what a security principal can do after being authenticated.

Authentication Factor An Overview Sciencedirect Topics
Knowledge factors are the most common factors used in user.

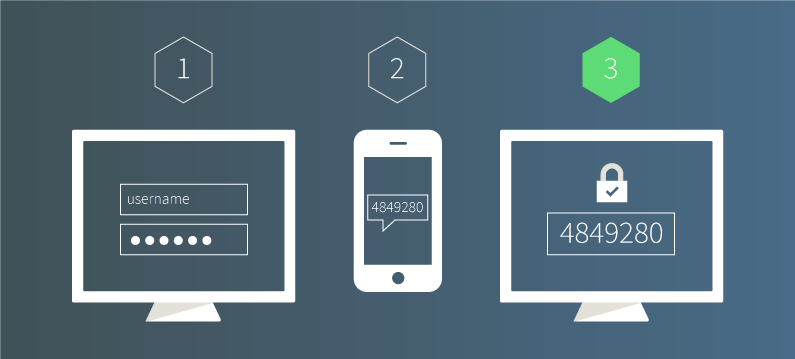
. Identify and describe the three basic authentication factors. Things you know knowledge such as a password or PIN Things you have possession such as a badge or smartphone Things you are inherence such as a biometric like fingerprints or voice recognition MFA Examples. The 3 types of authentication are.
Authentication ensures only authorized users are allowed into an organizations network. Approve or decline the authentication so the system can move to authorizing the user. This is commonly known as something you know something you have and something you are.
Requires the use of two of the three authentication factors. Historically MFA has demanded a choice of authentication mechanisms from at least two of the following categories. Represents the way that security principals prove their identity.
The process is fairly simple. Anything that you can remember and then type say do perform or otherwise recall when needed falls into this category. Currently used authentication factors include the following.
Authentication ensures only authorized users are allowed into an organizations network. Knowledge factors possession factors and inherent factors. Password basedContinuous authentication - Suppose a person logs into a website using its credentials and since most of the times cookies are not cleared and http protocol is persistent the details of credentials retain and so many times when the same person logs into the website he does not have to give the credentials.
The knowledge factor or something you know may be any authentication credentials that consist of information that the user possesses including a personal identification number PIN a username a password or the answer to a secret question. Knowledge something the user knows Possession something the user has Inherence some physical characteristic of the user. Describe the three types of authentication factors Type 1.
Provide screenshots of using md5sum in your group VM under your account 5. Is this really an appropriate name for the technology considering the function. 2Describe how the various types of firewalls interact with network traffic at various levels of the OSI model.
Something you know etc and provide examples. It is unlikely that an attacker could fake or steal all three elements involved in 3FA which makes for a more. In this method simply require users to verify their identity using a password.
1Define authentication and explain the three commonly used authentication factors. Explain the difference between authentication and authorization. Describe the five basic attacks on authentication systems.
Something you do is a type of authentication which proves identities by observing actions. Something the user knows eg a password partial password passphrase personal identification number PIN challenge response the user must answer. Most website authentication methods can be divided into one of these three categories.
Collectively these categories comprise the three types of authentication factors. Manage the connection between the human user and the websites server computer. Respond to the following in a minimum of 250 words.
This is possibly the factor that is the least utilized and probably not a lot of people know about it. That information is then sent to the authentication. There are generally three recognized types of authentication factors Type 1 Something You Know includes passwords PINs combinations code words or secret handshakes.
Knowledge factors possession factors or inheritance factors. Contains user accounts and their associated passwords in a workgroup model. Something you know such as a password Something you have such as a smart card Something you are such as a fingerprint or other biometric method Identification occurs when a user professes an identity such as with a username and authentication occurs when users prove their identity.
What is a DMZ. Can someone please help me with the following questions. Knowledge possession and inherence and most multi-factor systems feature at least two.
Authentication factors are traditionally split into three categories. Most MFA authentication methodology is based on one of three types of additional information. There are several factors used in authenticating a user.
There are generally three recognized types of authentication factors. Something you know etc and provide examples. Describe how password hashing works a.
Type 1 Something You Know includes passwords PINs combinations code words or secret handshakes. Multifactor authentication dramatically improves security. Users input their credentials on the websites login form.
Anything that you can remember and then type say do perform or. Three-factor authentication 3FA is the use of identity-confirming credentials from three separate categories of authentication factors typically the knowledge possession and inherence categories. As threats become more sophisticated it is critical to have strong authentication in.
There are three common factors used for authentication. The three factors classes and some of the elements of each factor are. Take note that they are categorized into three.
Describe the three types of authentication factors Type 1. Respond to the following in a minimum of 250 words. Computer Science questions and answers.

Authentication Factor An Overview Sciencedirect Topics

What Are The Three Authentication Factors Rublon
The 5 Factors Of Authentication Nowadays The Terms Multi Factor By Renan Dias Medium
No comments for "Describe the Three Factors That Can Be Used in Authentication"
Post a Comment